This week two new ransomware attacks have been detected, affecting both Mac and PC users. Ransomware has been a popular criminal business model targeting Windows users for while now, but a new ransomware, called KeRanger, is the first to specifically target Mac OS X machines. Meanwhile, in the world of Windows, PETYA, is a new and well-disguised ransomware affecting many unsuspecting victims.
Ransomware is a kind of a malware which imposes a lockout, preventing you from being able to use your computer until you pay a ransom or risk having your data completely wiped after the lockout period.
Both KeRanger and PETYA give victims a lockout window before total data destruction, demanding a ransom of 1 bitcoin to be paid (approximately 560.23 AUD at the time of writing).
Mac Users
The KeRanger malware was first discovered in rogue versions of Transmission, a popular BitTorrent client. Shortly after the discovery, Transmission requested all users running the version immediately upgrade or delete their copy, in case they have downloaded a malware-infected file.The attack is another demonstration of the risks involved with peer to peer file sharing, such as bit torrent. Whilst this particular attack has been limited to the Transmission bit torrent client, it is now not so hard to expect that future attacks may be spread through other file and email methods.
For Mac users, now is the time to be more vigilant about opening email attachments and website downloads.
PC Users
For those of you on PC, although ransomware is not new, it is now hiding in otherwise legitimate places! The nasty new ransomware, PETYA had been found disguised in an email disguised as a Job Applicant’s CV. The email links to a Dropbox folder containing the applicant’s ‘Curriculum Vitae’ which instead downloads the malicious file.
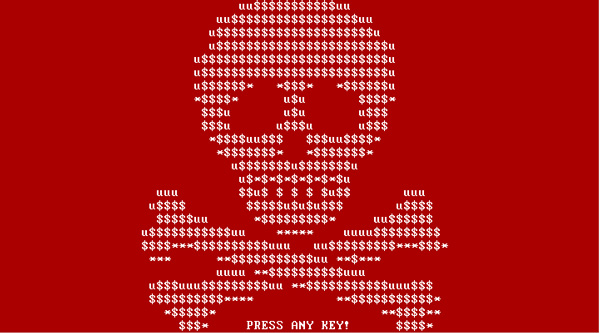
PETYA warning screen. Source: TrendMicro
For our clients with a Mac Aid Monitoring service, a report will be received if you have been affected by ransomware so that it can be resolved as soon as possible.



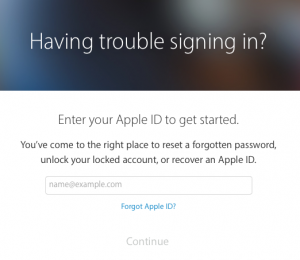
Once you’ve arrived at Apple’s recovery page, just type in your Apple ID and you can choose to either answer your security questions or have reset instructions emailed to a recovery email address, if you have previously supplied one.
For some of us, it’s not just the password we’ve forgotten, but also the ID itself! If this is the case, all you need to do is click on Forgot Apple ID? Here you’ll be prompted to enter your full name, email address and let Apple work it’s magic to find your Apple ID.
This week a new ransomware has been detected, affecting some Mac users. Ransomware has been a popular criminal business model targeting Windows users for while now, but this new ransomware, called KeRanger, is the first to specifically target Mac OS X machines.
 What is ransomware?
What is ransomware?Ransomware is a kind of a malware which imposes a lockout, preventing you from being able to use your computer until you pay a ransom or risk having your data completely wiped after the lockout period.
The KeRanger malware waits dormant in affected machines for 3 days before requesting the ransom. KeRanger then gives victims a 72-hour lockout window before total data destruction, unless a ransom of 1 bitcoin is paid (approximately 552.41 AUD at the time of writing).
The KeRanger malware was first discovered in rogue versions of Transmission, a popular BitTorrent client. Shortly after the discovery, Transmission requested all users running the version immediately upgrade or delete their copy, in case they have downloaded a malware-infected file.
The attack is another demonstration of the risks involved with peer to peer file sharing, such as bit torrent. Whilst this particular attack has been limited to the Transmission bit torrent client, it is now not so hard to expect that future attacks may be spread through other file and email methods.
For Mac users, now is the time to be more vigilant about opening email attachments and website downloads.
For our clients with a Mac Aid Monitoring service, a report will be received if you have been affected by the KeRanger ransomware so that it can be resolved as soon as possible.
