The flexibility to work from home is becoming the norm, and at times it can be required at short notice. It can also be a significant deciding factor in attracting great staff, as flexible working solutions are expected in many industries. For modern businesses, legacy phone systems and mobile phones can struggle to give your staff and clients the flexibility they need.

You are probably already using Microsoft Teams, maybe regularly as a way for your staff to keep in contact, or maybe for the occasional meeting. Did you know that by integrating Microsoft Teams Calling, it can become your phone system as well? Staff can make and receive calls on any device, Windows, Apple, iPhone, Android, Desktop, MacBook, iPad or tablet, no matter where you are or what you are using. All that is required is an internet connection, and your calls will reach you.
Calls are made directly to and from the Teams app to regular landline and mobile phone numbers, to multiple people at once if required. There is no need for staff to disclose their mobile phone number, which is especially important when you may require staff to use their personal mobile, something often resorted to out of necessity during unpredictable lockdowns. It also means staff in this situation are not left covering call costs.
The app is simple to use and can be configured and scaled to suit your business needs. It has all the attributes of a regular phone system, with much more flexibility and additional options to improve your work life. Importantly when making the switch to Microsoft Teams Calling, there is no need to change your phone number/s.
Work-life balance can be protected by configuring Microsoft Teams Calling to only ring during business hours.
Voicemail is available for unanswered and after-hours calls. Voicemails are transcribed and emailed to you as both a text and an audio file, which can be accessed and responded to at your convenience.
Properly staff your primary number during business hours, even when your people are scattered across several locations. Your business number can be configured to ring multiple staff members, ensuring important calls aren’t missed.
Easily transfer calls, no matter the location of the other staff members.
A move to Microsoft Teams Calling also means you can aggregate all your IT support with one provider, rather than needing separate resources for general IT and your phone system. When on-boarding or off-boarding staff, it is much more convenient to have one IT provider handle email, cloud and other services AND your phone accounts.
If your current phone system is no longer meeting your needs, talk to Mac Aid today to find out what a move to Microsoft Teams calling can do for your Business.
With the unpredictability of lockdowns and working from home, becoming more commonplace, it is essential to ensure that your home office set-up is working for you as best as it can. Getting things wrong can cause neck and back pain, eye strain, headaches, and other health issues. Even if you set up everything correctly initially, it is important to check in from time to time to make sure you haven’t let things slip, or if you haven’t thought about it much at all yet, now is the time.
Understandably, not everyone has the space or budget to acquire everything for the perfect home office set-up, but the more things you can get right, even by improvising as best you can, the better. If you have existing back or medical issues that may be affected by your work setup, you should consult with your medical practitioner regarding your specific needs.
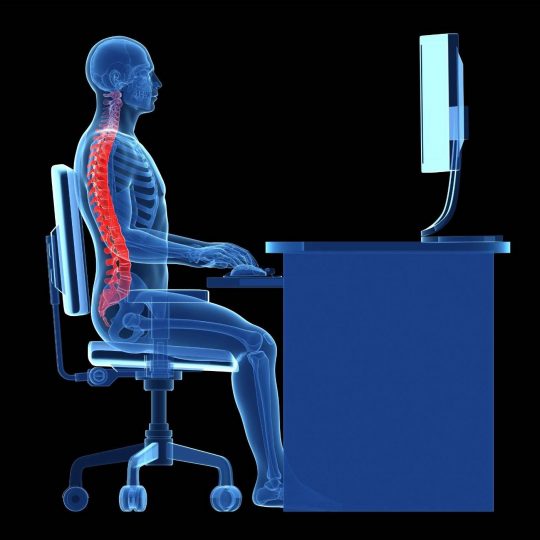
When sitting at your desk, or even if you need to use a table, if things are adjusted correctly you should be able to have relaxed shoulders, and your knees and elbow should create 90-degree angles. If you cannot rest your feet on the floor, you need to get a footrest, or you could even improvise one by stacking up some books or boxes to get the correct height.
Ideally, an office chair is best if you have space for one. When choosing an office-style chair, you should check it complies with the Australian standard AS/NZS 4438.
As well as being able to adjust it to your height requirements, the back of your chair should support the natural S curve of the spine. If it’s not possible to use an office chair, choose the best option for height and back support.
Many people working from home rely on their MacBooks, and while they are excellent for portability, looking down at your screen all day can cause neck issues. Ideally, having a separate, height-adjustable screen is best as well as a separate keyboard and mouse, allowing everything to be in an optimal position for your comfort. Your keyboard should be 8-10cm from the edge of the desk. If a separate screen is not an option, consider raising your MacBook on a stand or even a stack of books to get it to the correct height, of course, you will need a separate keyboard and mouse to be able to do this.
Your screen should be approx. 2-3 inches above your eye line. Although, if you wear bifocal glasses, you may need to lower this to a level appropriate for your vision.
Place your telephone in easy reach or use a headset if possible if you are required to use the phone often.
Our eyes aren’t designed to focus on close-up objects all day. Muscles control our eyes, when we are focusing up-close, we ask them to work extra hard, and just like any muscle, they get fatigued. Lockdowns and working from home lead to greater rates of eye strain as we are outdoors much less, no longer commuting as often, our eyes don’t get to relax and look off into the distance as often as they need to reset and relax. Eyestrain can lead to headaches, dry eyes, itchy burning eyes, eye pain, redness, and blurred vision. A great tip to help de-stress your eyes is the 20/20/20 rule. Every 20minutes, look at something 20 meters away for 20 seconds. Also, keep in mind that our blink rate can drop by half when we are fixated on a screen. When we aren’t blinking our eyes aren’t getting the lubrication they need. Be mindful about blinking more, you may also find that lubricating eye drops can help.
Other things you can do to reduce eye strain are to ensure your workspace is well lit, reduce glare on your screen, and experiment with the brightness of your screen, you don’t want it to be too bright. If you are in a room where the light conditions change through the day, remember to keep adjusting your screen to suit.
Having your office space set up ergonomically is great, but you do need to get up and move around periodically though out the day. Remaining in the same position for extended periods can inhibit blood flow and is not good for your body in general.
Get up and move around for 1-2 minutes every half hour, and take your lunch break away from your computer.
Chances are you use Preview all the time, someone sends you a PDF or an image, you double click to open it up, look at it and move on. It’s a simple app, but if you take the time to look around, you’ll realise it’s a very useful tool with quite a few handy features. You might even be paying for an expensive graphics app designed for impressive technical feats but just using it for basic tasks that are available to you right here for free.
Have you ever taken the time to look at what all those buttons in Preview do? While some of them are pretty obvious, like ‘Zoom’, ‘Share’, and ‘Rotate’, what about the others? From filling in forms or making notes on a PDF document to some quite handy photo editing tools, you may be surprised just how often Preview may be the program that can do exactly what you need.
Make the 
Here are just some of the helpful things you can do with Preview that you may be unaware of:
FILLING OUT FORMS AND SIGNING PDF’S
Have you been sent a PDF form to fill out and sign, but it doesn’t have those handy boxes that allow you to type directly onto the document? Or maybe it does, but then how do you sign it at the end? Hands off the print button, it can all be done right here.
REMOVING, ADDING OR MOVING PAGES IN A PDF
Preview isn’t just helpful when it comes to text, it also has some excellent photo editing tools. While it doesn’t compare to a tool like Photoshop, if you’re not a designer or photo editor, the simple tools available might be all you need.
SLIDESHOW
Some of the most common uses of an app like Photoshop are resizing and cropping images and saving them in different file formats. If that’s all you need, Preview can do that for you.
CHANGING THE SIZE OF AN IMAGE
CHANGE IMAGE FORMAT
CROP
IMAGE COLOUR CORRECTION
REMOVING A PLAIN BACKGROUND FROM AN IMAGE
SELECT PART OF AN IMAGE AND PLACE IT INTO ANOTHER:
This article is by no means everything Preview can do but is intended to give you an idea of what is possible. If you have found any of these tips helpful, have a bit of a click around yourself and discover what other tasks Preview can assist you with.
What is phishing?
You may or may not have heard the term “Phishing”, but you would have likely experienced at least attempts at it. Phishing is the term to describe a cybercrime in which the attackers send fraudulent emails, often posing as a legitimate business or a person that you know. The intention is to get the email recipient to disclose financial information, confidential security information or other sensitive information or even make payments directly to them. It can also entice you to click on an apparently important or urgent link that downloads malicious software onto your computer. A phishing email might send you fraudulent payment details for a contact you already have, meaning you send payments to their account instead of your intended recipient. Phishing emails can even be sent via the actual email account of someone you know if attackers have obtained their password and gained access to their email account, or they may have hacked in and are monitoring the mailbox.
Phishing attacks are on the rise, they are getting more and more sophisticated and increasingly harder to pick. You may find these days that most attempted Phishing attacks are sent straight to your junk folder by your email provider. If it’s your business email, it’s likely these emails will never see the light of day, which might make you feel safe. However, these days phishing attacks can look incredibly legitimate, even to your email filters, and are known to fool everyone from home users right through to CEOs on an alarmingly regular basis. The consequences of which range from large financial losses to incredible damage to your business’s reputation.
Phishing is something we will always need to be vigilant about. Security techniques to protect us are continually improving, but the attackers are constantly working out new ways to get past our defences. The cost to the attackers can be very low, and unfortunately, so is their chance of getting caught. In contrast, the financial gains can be incredibly high, often with minimal effort on their part, so it will likely always remain an attractive avenue for these people. Phishing kits can even be purchased on the dark web these days, allowing even a newbie scammer to launch a formidable and believable looking attack.
How can you protect yourself?
All of this can seem a bit scary, but fortunately, there are things you can do to prevent yourself from falling target.
What should you do if you have been compromised?
Immediately disconnect your device from the internet, either by unplugging the ethernet cord or turning off the Wi-Fi, or turning off cellular data. Depending on how you are connected. Unplug any external hard drive that you might be backing up to. This can help to prevent:
If this is within a business setting, alert your IT department straight away. They may take over from that point or give you instructions to follow. Delaying this step could be costly.
If this is a home computer, the best option is to call us to discuss what happened so we can advise what steps to take next. If you are unable to get in touch with us at the time and are confident with the process you may choose to do the following:
When it comes to phishing attacks, it is important to keep in mind that once you are compromised it doesn’t just affect you, it can quickly and easily become something that has a knock-on effect to friends, family, colleagues, or your business. If you feel you could be doing more to prevent attacks, but are unsure what the next steps are, reach out to us at Mac Aid to discuss how we can help.
Shadow IT put simply, is the use of non-approved software, hardware or processes by staff members without company knowledge to complete their work. Chances are, it’s happening right under your nose and could be putting your business at risk in many different ways.
It takes a great deal of time and money to set up IT infrastructure to ensure that you don’t leave your business open to security, continuity or compliance issues. Software, Hardware and processes are chosen carefully and monitored for these reasons. So, if staff are opting to use applications or solutions the IT department is unaware of it can lead to significant issues as it is impossible for these things to be monitored and they are outside of the confines of protected networks and security systems.
It could be as simple as a staff member that is an Excel whiz, creating a spreadsheet to do quick calculation when a lengthy manual calculation has become part of their job and no other solutions have been made available. It makes sense to them as it makes their job much easier, and they are much more efficient. Then other staff find out, it gets emailed around, everyone probably thinks it’s not only harmless but incredibly helpful. However, the accuracy has not been checked by the correct people, and what happens when changes need to be made to the calculation, potentially quite often? How do you make sure staff are using an up-to-date version when you don’t even know it exists in the first place? This is an invitation to costly and constant errors.
Shadow IT can also be people walking around with portable storage such as USB drives carrying sensitive information with no proper care for security, online messaging services, alternative online email, online VOIP software, and much more.
These days one of the biggest problems is rogue instances of cloud-based SAAS programs (Software as a Service). These are applications and services that are delivered over the internet, so are easy to access and simple to turn to for quick solutions. SAAS applications are run on the provider’s server and so they are responsible for security, performance and maintenance. Your sensitive business data could end up stored anywhere and not necessarily in a secure way. Data can get spread across different cloud services and apps that you are entirely unaware of, leaving you open to security and compliance issues. Staff might set up these services with very simple or repeated and widely shared passwords.
Even if the service they use is secure, it can cause inefficiencies. For example, you might have a file sharing service set up, such as DropBox, but some staff choose to use a different cloud service, resulting in multiple versions of documents being created and circulated, making workflow inefficient and introducing the risk of the wrong versions of files being used. Other teams may not have access to what they need, and of course, should a staff member leave, you may lose access to the work they did.
If you’re assuming Shadow IT happens because ‘bad’ employees just don’t care about the rules, think again, that can be a reason, but that is far from the leading cause.
Shadow IT can occur for a lot of reasons. In many instances, staff members may not even realise they are doing the wrong thing, they are simply being resourceful and getting things done in what seems to them the easiest or most sensible way.
It could be that all the correct software or solution is available, but some staff are unaware it exists. Maybe they don’t know how to use it properly, or perhaps what you are providing is simply inadequate.
Keep in mind that Technology is ever-changing, you need to keep up, and if what you have in place doesn’t meet the needs of your staff, they are likely to find a workaround. And why wouldn’t they? Let’s face it, in today’s fast-paced world, everyone is striving for work/life balance, and it is tough to achieve. Working smarter rather than harder is everything. If your staff perception is that they are working with inadequate IT systems and processes and they feel they will have far less time with their family because of this, then it will not come as a surprise that people will try and be resourceful and look for alternatives. If staff are facing working longer hours than necessary to complete a task and find an app that’s going to help them out, it’s very likely they will be signing up.
As mentioned, staff may be unaware this is an issue, so the first step is comprehensive and ongoing training. Educate them properly AND have the correct tools in place, then there’s no need for them to look elsewhere.
Another important step is having a system in place where staff can request to have new software/hardware added to the approved list if they need it. Make this part easy, it will save you a lot of headaches. Some businesses have a hardline approach to Shadow IT, which still doesn’t stop it from happening, it also ignores that Shadow IT is actually generally highlighting that there is an issue within the business that needs to be solved rather than just shut down.
It can all sound pretty scary, but it truly isn’t all bad. In many ways Shadow IT can be seen as an opportunity for business growth. The vast majority of staff don’t want to be doing the wrong thing, they just want to get their job done as efficiently as possible. Consider why people are using other solutions. Is it actually shining a light on inadequacies within your business processes that need to be addressed?
Obviously, a big part of dealing with this is knowing it’s happening in the first place, the sooner problems are found the less harm they are likely to cause. It is important to be open to suggestions for changes and improvements from employees. They are the ones doing the work of your business, and possibly more aware than you might be of the efficiency impacts of the services and processes your business is using.
So, are there methods to identify shadow IT? Absolutely, there are many tools available, and importantly there are ways it can be done sensitively and without invading an employees’ privacy. Potential issues can be flagged which gives you the opportunity to have the possibly awkward but very necessary conversation with the relevant employees. Remember, once it is identified, take the opportunity to think about what it means how you can improve your business moving forward.
If you are not already actively seeking to identify Shadow IT within your business or you have concerns, contact us today to discuss your options.